1. Web applications are used in modern organizations to improve the user experience and provide critical business functionality. Unfortunately, both small and large-scale organizations don’t prioritize security testing of their web applications. As a result, attackers can easily compromise these applications, disrupt business functionality, and gain unauthorized access to sensitive data.
As numerous organizations falsely trust in the accuracy of automated web application security scanners, they’re left with unidentified loopholes in their application’s functionality, source code, and infrastructure. It’s critical that you conduct manual penetration testing before deploying your web applications in production.
2. As an organization, you face a number of challenges in the world of web applications. You need to meet the demands of your users while also providing them with a secure and reliable user experience. This can be difficult, particularly when you’re dealing with large-scale applications that are being developed by multiple teams. As more and more organizations rely on these applications, they can become more vulnerable to attacks from hackers who want to compromise your business and steal sensitive data.
To help you stay ahead of this challenge, we offer a variety of services that allow us to analyze your web applications for vulnerabilities, identify missing security features, and help you create a plan for how you can improve your overall security posture.

A penetration testing is a methodical process that involves identifying security flaws in web applications. A penetration tester or cyber security specialist evaluates an application’s security by exploiting it, just like an attacker would. For example, the specialist will look into how an unauthorized person could acquire access to the application’s sensitive data.
For this purpose, a web application penetration test helps organizations to find security flaws in applications that could be readily exploited by adversaries. At the very least, a web application penetration test includes checks for the following vulnerabilities (included in the OWASP Top 10 Web Application Security Risks):
Web application penetration tests are security assessments curated to analyze the architecture, design, and configuration of web applications. Our team makes use of advanced web application security skills necessary to perform a manual and thorough penetration test against modern web applications. Further on, we offer code-assisted penetration tests to explicitly understand the application, detect deep-seated issues in source code, and reduce the number of false-positive findings.
Our clients include large corporations that need to ensure their websites are secure from external threats. We also work with smaller businesses who want to know if their website holds up against an attacker trying to gain access through weak passwords or other vulnerabilities in their systems.
At Indian Cyber Intelligence , we leverage the following testing methodologies:
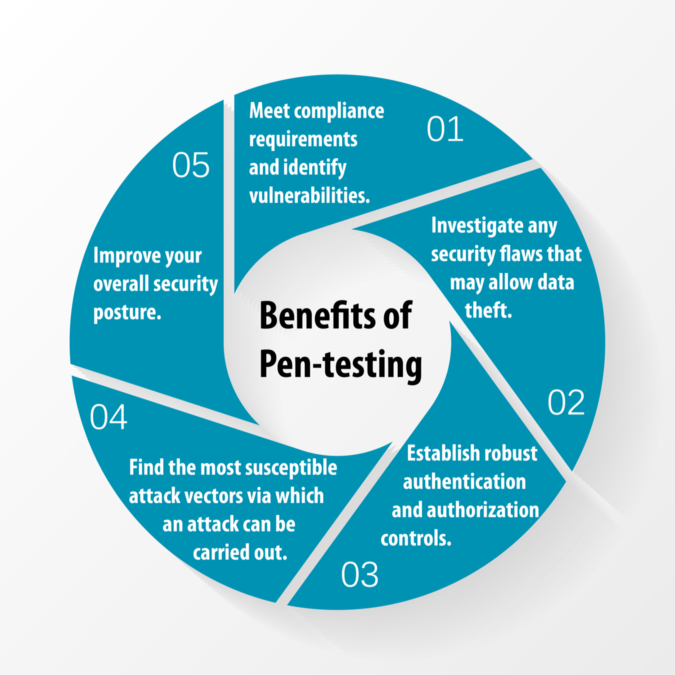
Our team makes use of advanced skills necessary to perform a manual and thorough penetration test against modern web applications. To add, we follow OWASP’s standards for web application security.

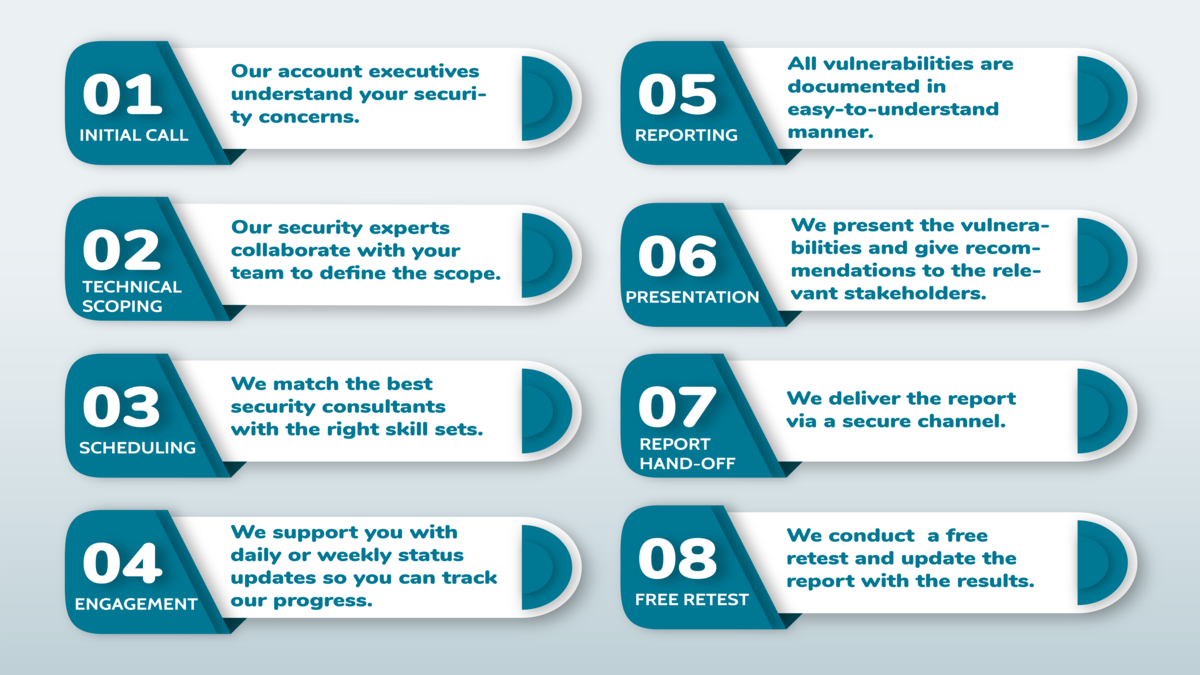

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.