The API attack is one of the most significant threats to an organization’s IT infrastructure and data. This type of attack allows adversaries to exploit vulnerable endpoints and also the underlying applications associated with such API endpoints. Once these API endpoints are maliciously bypassed, attackers can gain unauthorized access to the sensitive data stored within the underlying applications. They can damage application functionality, abuse business logic, and in certain circumstances, access and threaten an organization’s internal infrastructure. Adversaries proficient at exploiting insecure API endpoints can make any business vulnerable to consistent attacks.

API penetration testing is a process that identifies vulnerabilities in your APIs and creates secure endpoints. The reason why this is so important is because API abuse is one of the most prevalent application risks. It can wreak havoc on the normal operation of any digital enterprise.
If your deployed APIs are not thoroughly tested for security, problems such as data leakage, unauthorized access, and parameter tampering might develop.
The goal of an API penetration test is to find ways to exploit an API’s functions and methods as well as circumventing its authorization and authentication mechanisms. At the very least, you will want to find ways to break out of the application, an API penetration test includes checks for the following vulnerabilities (included in the OWASP API Security Top 10):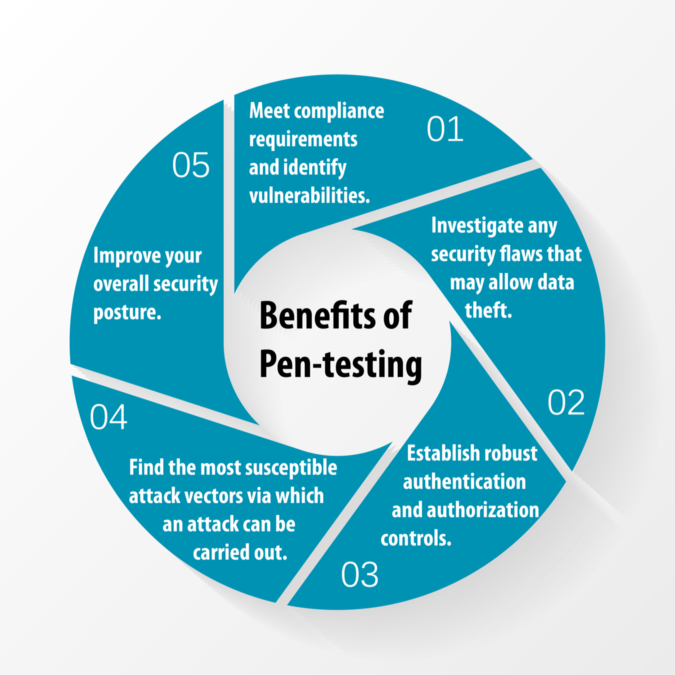
Our team makes use of advanced skills necessary to perform a manual and thorough penetration test against modern web applications. To add, we follow OWASP’s standards for web application security.

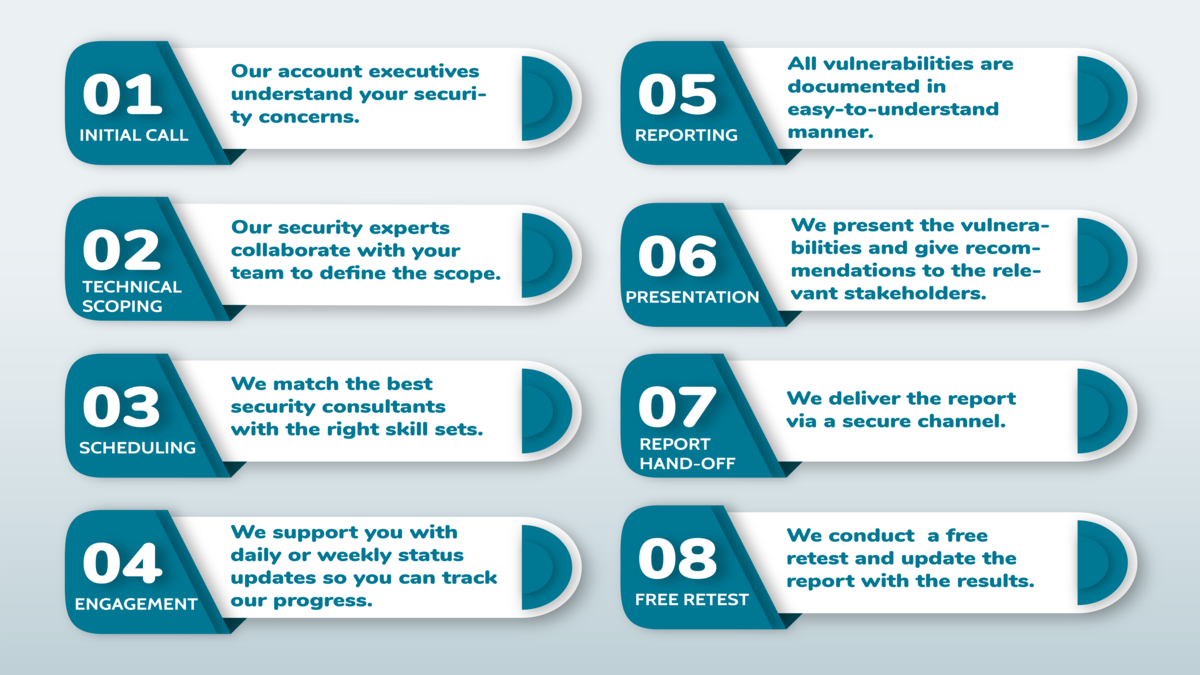

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.