Kubernetes is vital to automating varying elements of application deployment and offers a plethora of business benefits. However, misconfigurations in the Kubernetes platform make it susceptible to attacks. Despite the deployment benefits offered by the Kubernetes platform, misconfigured environments can be under constant attacks and adversaries can move laterally to compromise an organization’s valuable assets.
The security of your Kubernetes platform is just as important as the security of traditional environments.

Securing your Kubernetes environment is no easy task. It's a lot of work to do it right, and there are tons of things that can go wrong.
We've got you covered when it comes to securing your Kubernetes environment. Our services include:

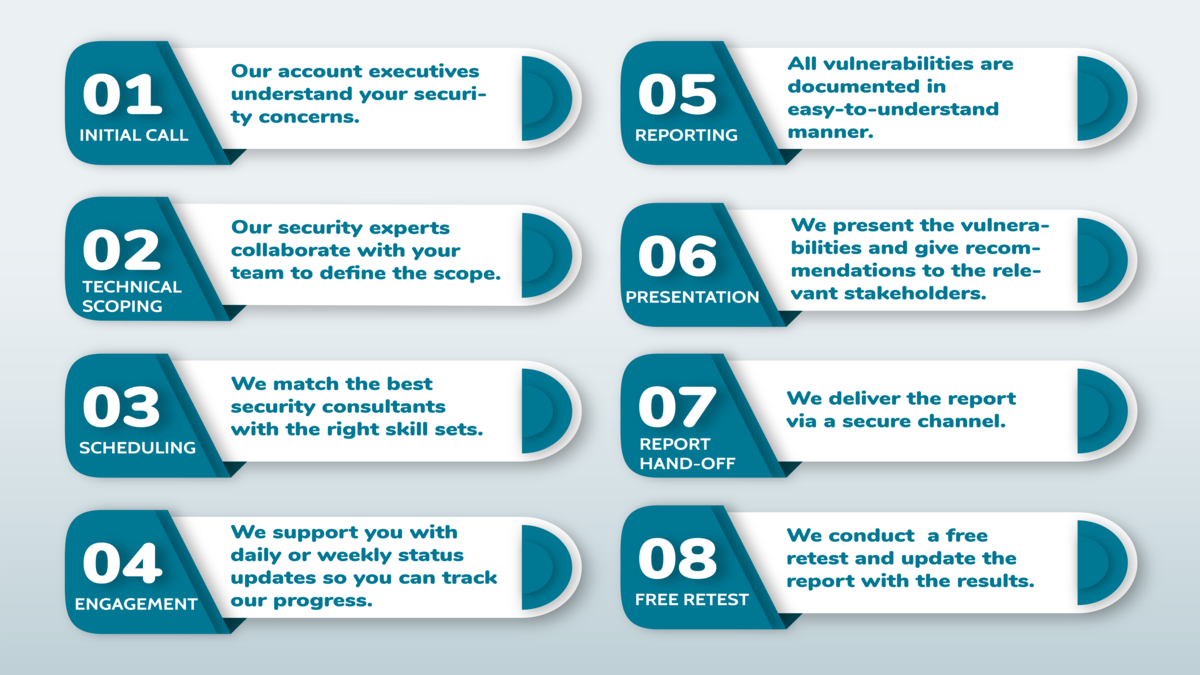

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.