Open source intelligence (OSINT) is a data gathering and collation technique that focuses on publicly accessible sources. Common sources include, but not limited to, social media platforms, published content, company websites, forums, and also the dark web, with an end goal to find any information that could pose a risk to an organization.
This form of intelligence gathering has been widely used by organizations such as government agencies and law enforcement services for years now. This technique can be used for various purposes including but not limited to:
-Information gathering about competitors' products and services
-Gathering information about potential threats such as hackers or cybercriminals
-Identifying potential partners or business opportunities
The gathered data is then combined, normalized, structured, and further analyzed to test the target organization’s operational security. In simpler terms, the data is harvested, enriched, and reported to collectively study the scope of attacks the organization can fall victim to. OSINT can be a part of red team engagements or advanced external network penetration tests.
OSINT is a part of information security that collects and analyzes publicly available data about an organization or person. It helps organizations understand their exposure to cyber-attacks by identifying potential vulnerabilities in their systems and processes. OSINT can be used by governments, corporations and private individuals to research potential targets.
At Indian Cyber Intelligence, we believe that the best way to protect your business is to stop threats before they happen. We use cutting-edge OSINT strategies to extract vulnerable touchpoints so organizations can mitigate these risks before such information can fall into the wrong hands.
Our experts are trained to use the latest tools and techniques to identify vulnerabilities in your organization's security, so you can make sure you're always protected against the latest threats and zero-day exploits.

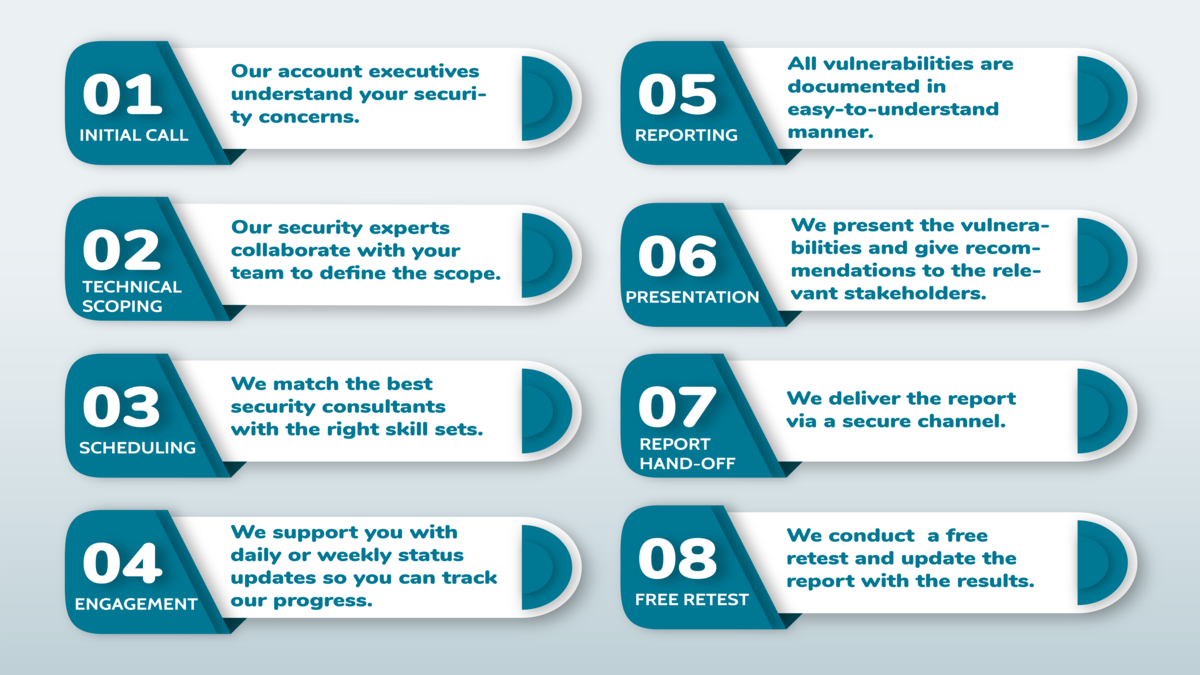

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.