When you think about your organization’s security posture, do you consider the possibility of a breach that would occur outside of your perimeter?
Most businesses prioritize defending their environment’s perimeter from external threat actors. But what if that perimeter is breached?The foundation of your organization’s security posture is a secure and a robust infrastructure. As technology progresses, hackers devise more complicated strategies to breach an organization’s security defenses and cause havoc. To prepare for this growing threat, you must think like an adversary. And the best way to achieve this is via an internal network penetration test.
A penetration test will help identify vulnerabilities in your network ahead of an actual breach by testing whether or not systems are protected against attacks from within or outside the network. This can help reduce the risk of future incidents occurring within your organization when there is already damage done through a compromised system outside of your control.
An internal network penetration test is more than just a vulnerability scan.
It's an advanced infrastructure assessment that helps to gauge what an attacker could achieve with an initial access to a network, including the possibility of gaining access to sensitive assets located in the internal network. Internal penetration tests involve privilege escalation, malware distribution, MiTM attacks, lateral movement, sensitive data exfiltration, and other harmful activities.
At Indian Cyber Intelligence, we believe that security is not just a buzzword.
We know that your business depends on the security of your network and systems, which can't be treated as a black box. You need to know what's coming in and out of your network, and how it's being used. That's why we go beyond traditional vulnerability scans and often deliver objective-based assessments depending on the scope of work. This includes obtaining "Domain Admin" privileges, or obtaining PII data within the internal network. We recommend carrying out frequent internal network penetration tests to discover and assist remedy vulnerabilities, given the financial repercussions of a breach.
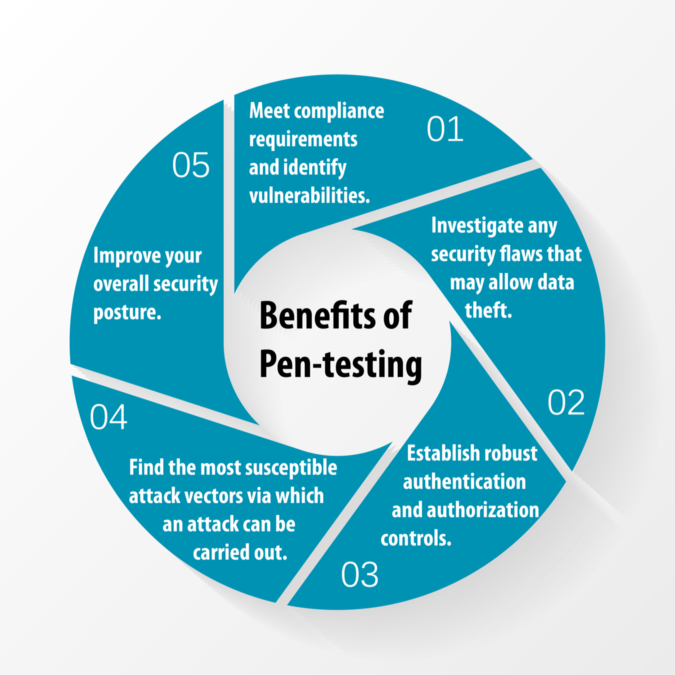
We believe that a successful penetration test begins with the client. We start by gathering as much information about your company and its business processes as possible, including information about your network architecture, security controls, and network vulnerabilities. We then perform an internal network penetration test to identify vulnerabilities and exploitation paths.
Our unique approach combines the best practices of traditional penetration testing with the latest tools and methodologies in order to create a report that allows an organization to assess its business risks.

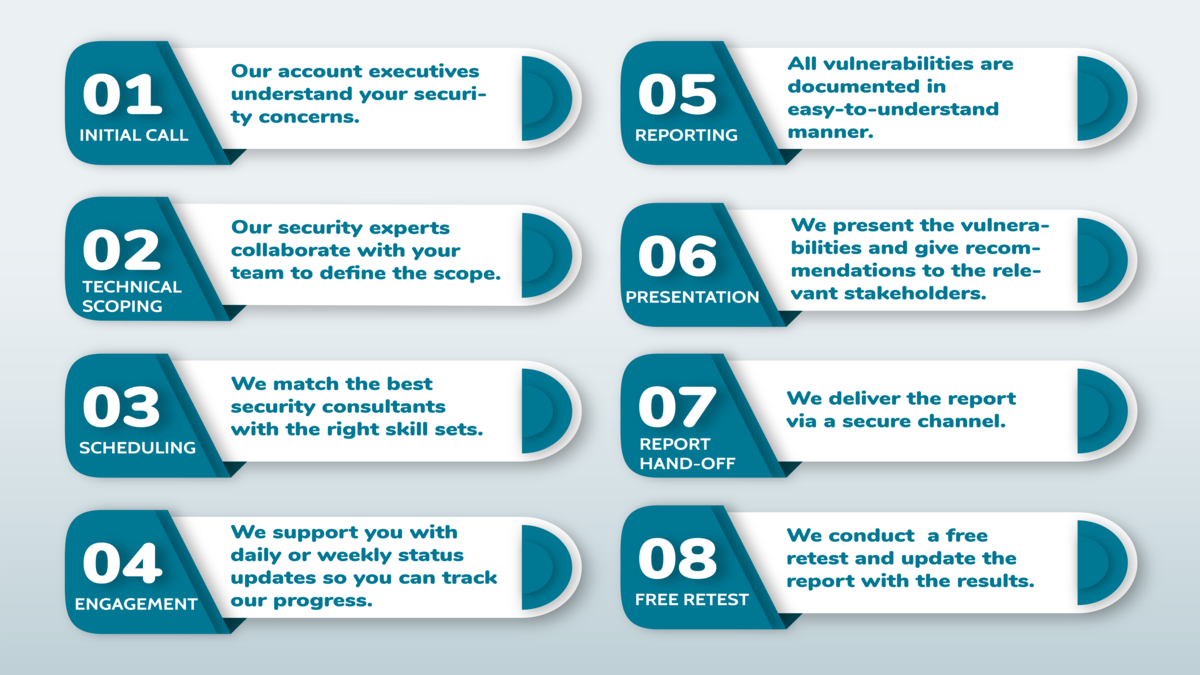

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.