The cloud is an amazing tool. It's incredibly flexible, scalable, and efficient. But it's also a potential security nightmare.
The more complex your cloud platform becomes, the more vulnerable it becomes to exploits launched by adversaries. And with rapid evolution of cloud-based environments, security challenges are growing in complexity by the day. This leaves organizations vulnerable to security threats, which can eventually negate the advantages of cloud platforms.
At Indian Cyber Intelligence, we're dedicated to helping you craft a cloud strategy that works for your business—and keeping your organization as secure as possible in this new era of digital transformation!
An application’s business context and security standards are assessed during a Cloud Configuration Review. The assessment includes interviewing key internal stakeholders and then analyzing the relevant cloud infrastructure using both manual and automated tools. The review involves finding configuration issues in the following areas:
These assessments are created using a mix of manual and automated methodologies that take into account industry best practices and security standards from trusted sources (such as the CIS Benchmarks).
Cloud security is a complex issue, but it's also one of the most important issues you'll face in your business.
Cloud Security assessments can be intimidating, but they don't have to be.
We offer organizations a comprehensive assessment of their cloud environments. This includes assessing your cloud configuration settings against industry best practices to keep your organization safe from cloud-based cyber-attacks.
We'll help you understand how to keep your data safe and secure in the cloud, and how to implement policies that prevent unauthorized access to your data—and all of this at an affordable rate!
We regularly review and update our methodologies to ensure that it’s aligned with the latest compliance and regulatory standards that many businesses must meet when implementing cloud services.
We offer the following services:
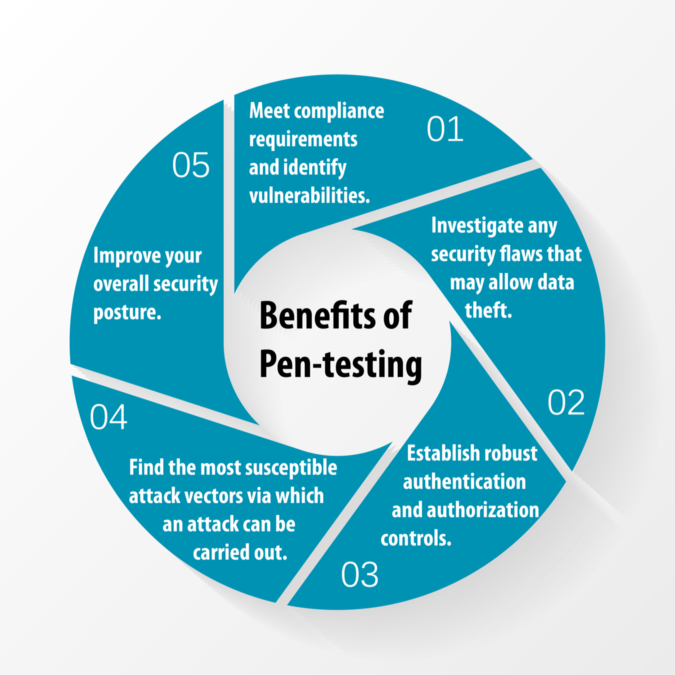
At Indian Cyber Intelligence, we know that the cloud is here to stay. And we know that you're looking for a way to configure and assess your security posture in the cloud, identify vulnerabilities and risks, and determine next steps to strengthen your security posture.
We've got you covered. We offer cloud configuration and assessment services to our customers in order to carry security into the cloud, identify vulnerabilities and risks, and determine next steps to strengthen their security posture.

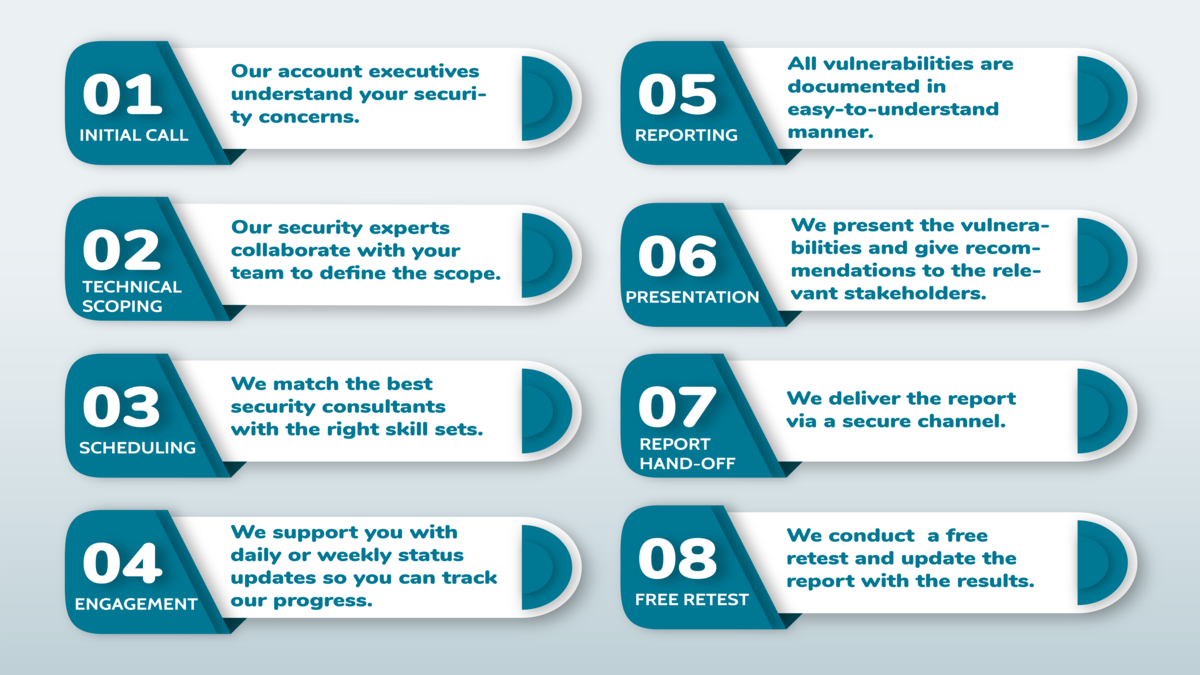

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.