Source code reviews reveal deep-seated attack vectors through code-design flaws, misconfigurations, vulnerable dependencies and dangerous code functions. Identifying such vulnerabilities during the initial phase of an application development, can strengthen an organization’s security posture and keep attackers at bay.
Even better, source code reviews can help organizations assess larger attack surface areas, accurately resolve security flaws and ensure that your development teams follow secure coding practices.
At Indian Cyber Intelligence, we offer source code assisted penetration tests to thoroughly understand an application’s attack surface, analyze its response to malicious input, scan for dangerous functions, detect deep-seated functional issues, and reduce the number of false-positive findings. This helps acquire a broad understanding of application’s readiness to deal with attacks.

Our team makes use of advanced skills necessary to perform a manual and thorough penetration test against modern web applications. To add, we follow OWASP’s standards for web application security.

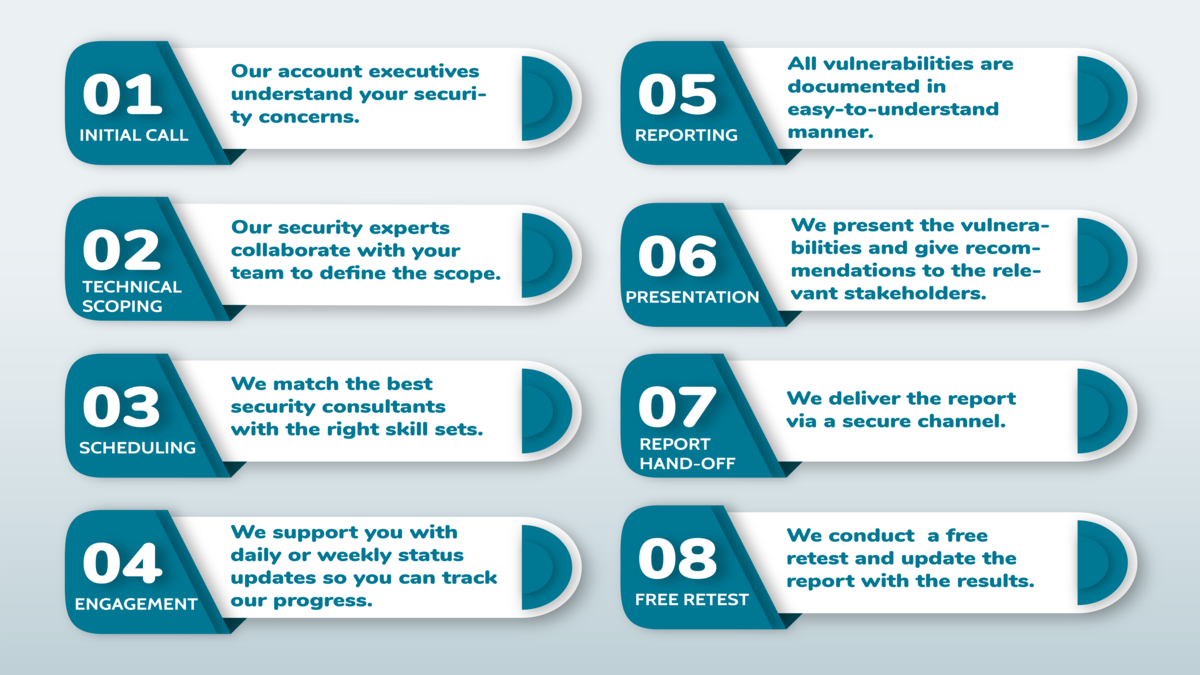

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.