Mobile applications are becoming more and more important to our day-to-day lives, but many consumers aren't aware of the security risks posed by their apps. According to a recent survey on app security, nearly two-thirds of mobile app users think that their health and finance apps are safe enough.
Security is a huge concern for many businesses, but one that can be easily overlooked. If we don’t understand how our apps are built and evaluated, we might misconstrue the severity of security issues as they arise.
In truth, installing and utilizing untested apps can put you and your company at risk. Untested apps may include security flaws that expose your data—and those flaws could be exploited by hackers or other malicious parties looking to steal your information.
Mobile apps are a different beast. While web apps can be hacked by simply visiting the website, mobile apps require a different methodology and setup than attacking web apps. Penetration testing might help us feel more secure, but breaking into mobile apps requires a different methodology and setup than attacking web apps.

Mobile application penetration testing is an essential tool that organizations can use to reduce their security risk and enhance their application security posture. The goal of a mobile app penetration test is to identify and mitigate vulnerabilities in client-side and backend server functionality, as well as deliver actionable recommendations for improving your application security risk posture. Before giving your mobile app to the end-user, it's vital that you run a mobile pen test to uncover any vulnerabilities that may need to be addressed before releasing the product.
When it comes to mobile apps, there's a lot of opportunity for hackers to exploit security flaws. A mobile application penetration test can assist in identifying security flaws in apps that could be easily exploited by attackers. It should at the very least contain checks for the following vulnerabilities (included in the OWASP Top 10 Mobile Application Security Risks):
At Indian Cyber Intelligence, we're all about helping you stay ahead of the game. We provide mobile application penetration testing on both iOS and Android platforms to uncover and address your security vulnerabilities so you can focus on business operations, stay ahead of adversaries, and keep your users safe.
We have a dedicated team of professionals who are experts in the field of mobile application penetration testing. We believe that the best way to detect vulnerabilities is by using a detailed manual approach. This approach aids us in enumerating and exploiting deep-seated vulnerabilities that are often missed by automated scanners. We detect not only common security issues but also business logic flaws. Remediating these issues assists organizations in improving ROI, enhancing customer experience, combating data breaches, and ensuring smooth application functionality.
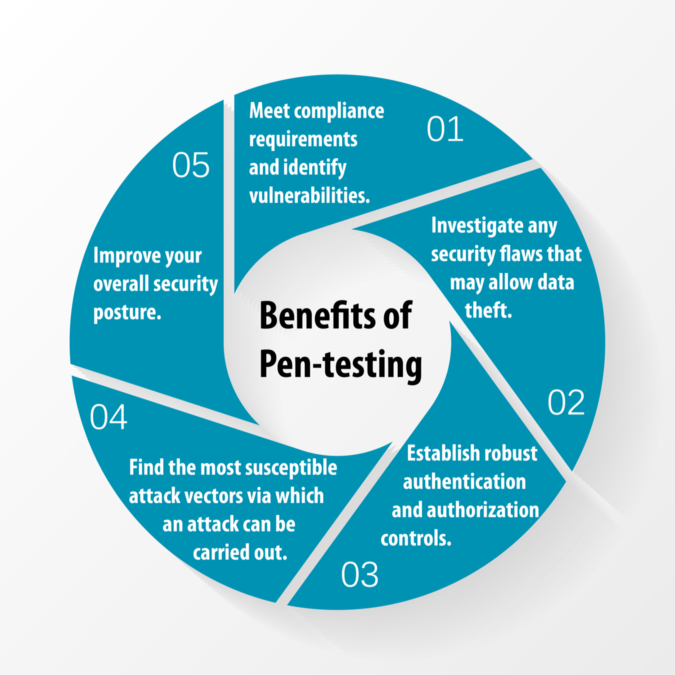
Our team makes use of advanced skills necessary to perform a manual and thorough penetration test against modern web applications. To add, we follow OWASP’s standards for web application security.

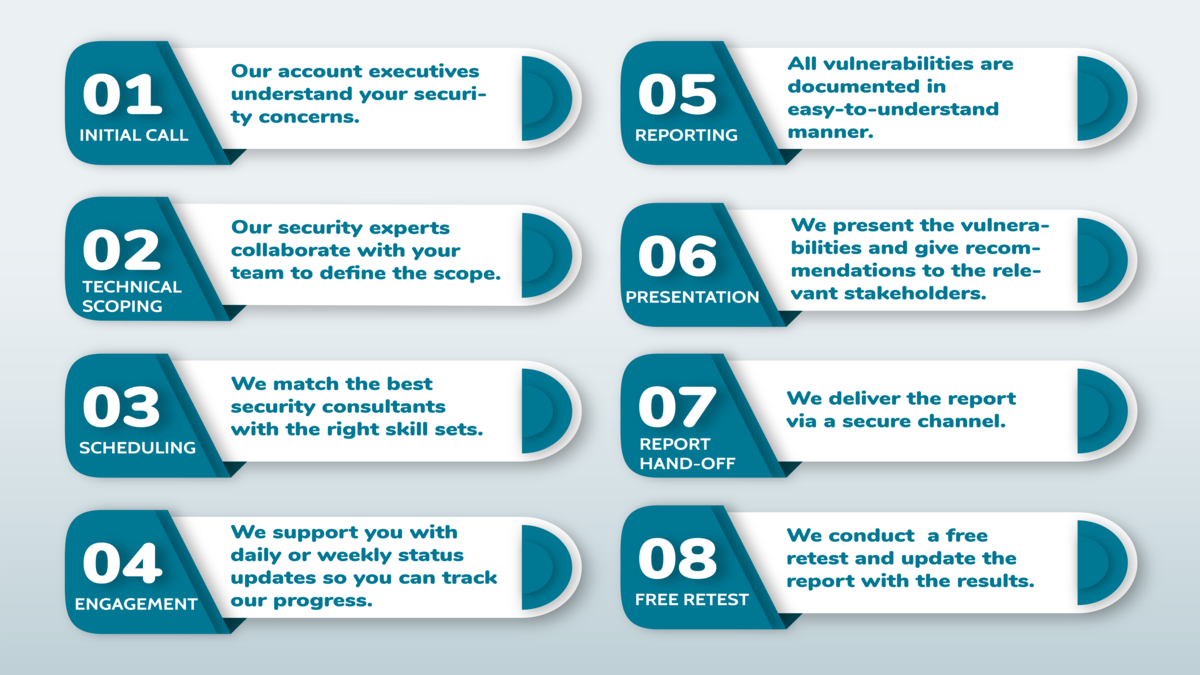

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.