The threat landscape is constantly evolving. Advanced attackers use sophisticated methods to get inside your network—like malware hidden inside emails or fake websites that trick employees into entering credentials into a malicious login page—and then move laterally across systems. This can allow them to access sensitive information like intellectual property or confidential business plans before it becomes public knowledge.
Adversaries use advanced tactics, techniques, and procedures (TTPs) to covertly exploit weaknesses in security controls, organizational security awareness, and bypass the internal security team’s detection and response capabilities. Apart from relying on social engineering attacks, modern adversaries also target publicly accessible services such as email and web servers, VPNs, and Office 365 environments. After gaining an initial foothold, adversaries attempt to bypass endpoint protection and move laterally within a network.
The good news is that security teams have access to a range of tools that can help them detect these threats before they do any damage—but only if they know how to use them effectively! In this course we'll show you how to use these tools effectively so you can reduce your organization's risk profile associated with advanced persistent threats (APTs).
The good news is that security teams have access to a range of tools that can help them detect these threats before they do any damage—but only if they know how to use them effectively! In this course we'll show you how to use these tools effectively so you can reduce your organization's risk profile associated with advanced persistent threats (APTs).
The ultimate goal of an attacker is to gain access to an organization’s critical assets. Thus, it’s clear how businesses should be abreast with their readiness for such attacks.
We deliver red team engagements to assess an organization’s preparedness to advanced persistent threat (APT) attacks. We do this by emulating real-world attackers’ TTPs used by cybercriminals and malicious insiders.
Our team of experts leverages their experience in the field of information security, intelligence gathering, penetration testing, and social engineering to emulate real-world attack scenarios that can be used against your organization. We simulate these scenarios in order to better understand where your organization is vulnerable and what steps need to be taken in order to protect it from a real attack.

To test your defenses, we create and design customized attack scenarios, as per the rules of engagement (ROE), which are best suited to your organization’s security posture.
These scenarios are designed to simulate real-world threat actors, so they challenge your security team in ways that are not always obvious—and they target the most vulnerable areas of your network.
We also offer a full range of technical solutions that can help you plug these holes and keep your systems safe from real-world threats.

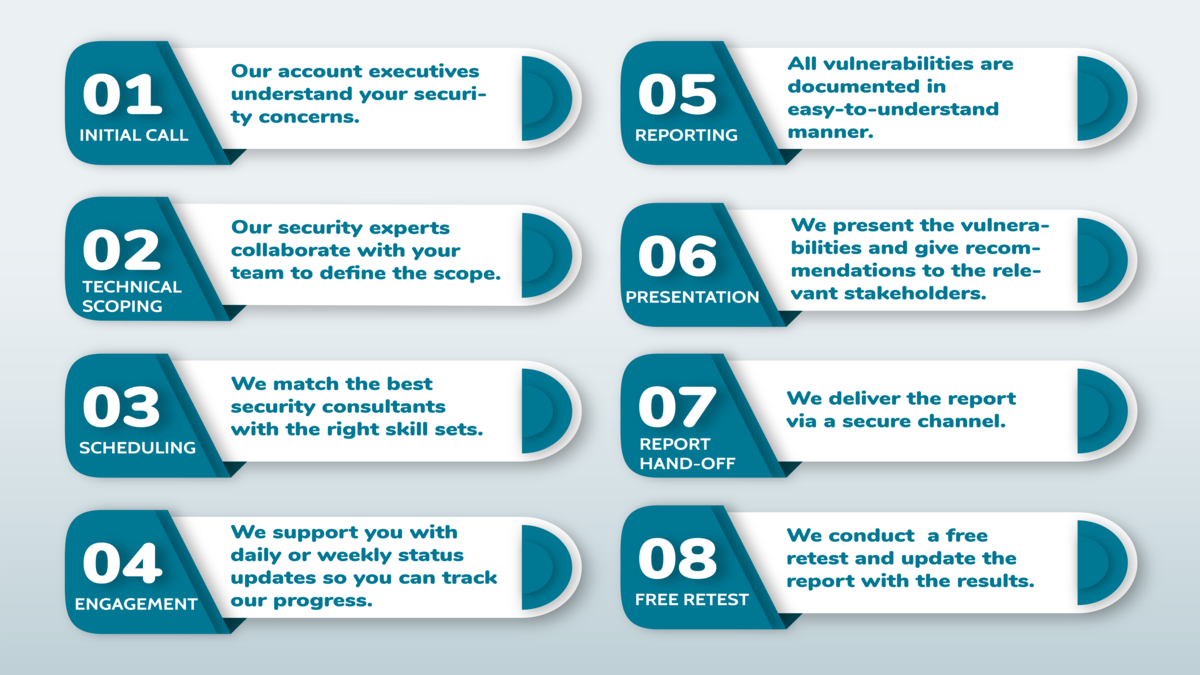

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.