Container Security is a continuous process of safeguarding containerized applications from prospective threats. It manages risks through CI/CD pipelines, container network infrastructure, its management stack as well as the applications running on such containers.
Container Security is not just another run-of-the-mill security solution; it is an end-to-end solution that provides both preventive and detective measures against cyber threats targeting your application's data.
As more and more organizations adopt container technology, this significantly increases the threat landscape. Adversaries can exploit a vulnerable container application and position themselves to access your organization’s infrastructure or move laterally through your cloud environment. Such security risks can arise through your container preparation, development, and deployment phase.
To ensure that your containers are secure, you need to perform vulnerability assessment during all stages of the container lifecycle—from setting up the environment to deploying applications in production. This includes:

We conduct a multi-layer container security assessment that involves a comprehensive review of your container environment.
We are here to help you achieve the security, compliance, and governance goals you need to be successful in today's digital world. Our team will work with you to identify any gaps in your container security strategy and create a plan to address them.

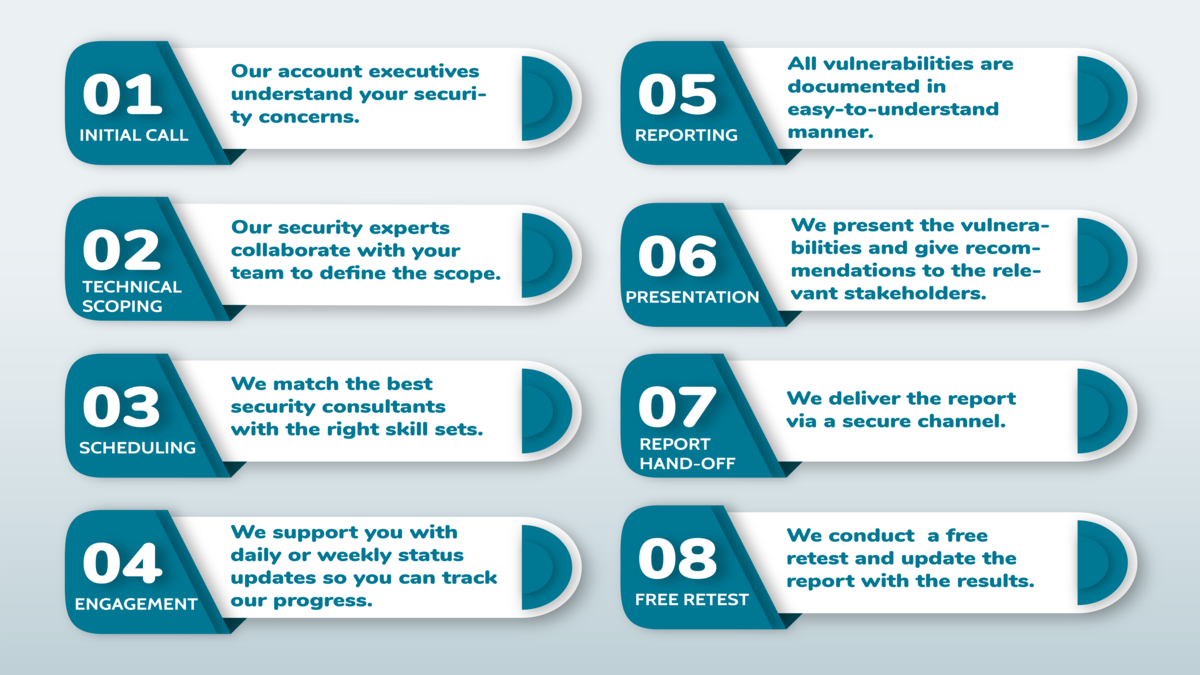

At Indian Cyber Intelligence, we believe that a thorough, in-depth report can help organizations make better decisions. That's why we create reports that display all technical findings in detail, with the relevant risk ratings and descriptions. Every report follows a strict QA process to ensure quality, accuracy and correctness. At a high-level, our reports include the following sections:













Copyright 2023 Indian Cyber Intelligence.